12 KiB
Tooling setup
- Setup home directory structure
- Install base packages
- Restore ssh keys and dotfiles
- Optional configuration
This guide will walk through how I setup fresh installations of POP!_OS. Pop!_OS is a free and open-source Linux distribution, based upon Ubuntu, and featuring a customized GNOME desktop environment known as COSMIC. The distribution is developed by American Linux computer manufacturer System76. Pop!_OS is primarily built to be bundled with the computers built by System76, but can also be downloaded and installed on most computers.
Pop!_OS provides full out-of-the-box support for both AMD and Nvidia GPUs. It is regarded as an easy distribution to set up for gaming, mainly due to its built-in GPU support. Pop!_OS provides default disk encryption, streamlined window and workspace management, keyboard shortcuts for navigation as well as built-in power management profiles.
I use POP!_OS as my daily driver operating system on a variety of different machines. The intent of this guide is to make it easy for me to get back up and running quickly whenver I do a fresh installation.
Setup home directory structure
After installing the distribution I ensure the following directories are present in my home folder as they are relied on by other automated steps in this setup process:
# Ensure we are in our home folder and create required directories
cd ~/ && mkdir Documents DownloadsInstall base packages
Now that we have our home directory done let's install the standard packages we use.
sudo apt install --yes btop nvtop screenfetch git curl wget xclip wl-clipboard xsel emacs xterm xtermcontrol jq tmux apt-transport-https dict gh unrar ripgrep
For working with container images locally outside of kubernetes clusters we use podman so that we can avoid the security problems of a standard docker daemon. Follow the steps below to install podman:
# Add the repositories to our apt sources
echo "deb https://download.opensuse.org/repositories/devel:/kubic:/libcontainers:/stable/xUbuntu_20.04/ /" | sudo tee /etc/apt/sources.list.d/devel:kubic:libcontainers:stable.list
# Add the repository key
curl -L "https://download.opensuse.org/repositories/devel:/kubic:/libcontainers:/stable/xUbuntu_20.04/Release.key" | sudo apt-key add -
sudo apt update && sudo apt --yes install podmanWhen working with kubernetes applications we often use helm, let's download and install the latest release from github.
wget $(sed 's/.\{1\}$//' <<< $(curl -s https://api.github.com/repos/helm/helm/releases/latest | grep -oP 'https...get.helm.sh.helm-v\d+.\d+.\d+-linux-amd64.tar.gz[)]'))
tar xf helm*.tar.gz linux-amd64/helm --transform 's,linux-amd64,,' && rm -rf helm-*linux-amd64.tar.gz
sudo mv helm /usr/local/bin/helm
Finally, we should upgrade the python package manger pip that we installed, before using it to install podman-compose.
sudo pip install --upgrade pip && sudo pip3 install podman-compose
For managing secrets we use bitwarden which provides a great cli utility. Additionally in our bashrc file included in this repository there are a number of helper functions to make working with bw easier.
# Download the latest release
wget "https://vault.bitwarden.com/download/?app=cli&platform=linux" --output-document "bw.zip"
# Unzip and install the latest release
unzip "bw.zip" && sudo install "bw" "/usr/local/bin" && rm "bw" "bw.zip"
# Login to bitwarden
bw login mail@jamesblair.net
For ad-hoc system administration we use ansible. We install ansible via pip3 to ensure any modules or additional packages required at a later date can be easily managed.
For significant ansible or python projects a virtual environment for python is suggested to keep project packages separate from system python packages.
pip3 install ansibleRestore ssh keys and dotfiles
I make extensive use of .dotfiles to further customise my environment. The script below restores my versions of key dotfiles automatically.
Obtain ssh key from bitwarden
In order to be able to clone the repository in the next step we need to obtain our ssh keys from bitwarden. Given we have installed the bitwarden cli we can mostly automte this process minus the initial login to bitwarden.
# Ensure we have an ssh-agent running
eval `ssh-agent`
# Generate a new blank key to overwrite
ssh-keygen -t rsa -f ~/.ssh/james -q -P ""
# Ensure we have an active bitwarden session
export BW_SESSION=$(bw unlock --raw > ~/.bw_session && cat ~/.bw_session)
# Export both keys
export key=$(bw get item desktop --pretty | grep notes)
# Extract private key
export private=${key:12}
export private=${private/END RSA*/END RSA PRIVATE KEY-----}
echo $private | awk '{gsub(/\\n/,"\n")}1' > ~/.ssh/james
# Extract public key
export public=${key/*ssh-rsa/ssh-rsa} && echo ${public::-2} | awk '{gsub(/\\n/,"\n")}1' > ~/.ssh/james.pubClone and restore dotfiles
Once our keys are available to us we can clone down our dotfiles and get back to our comfortable normal terminal environment.
# Clone down this repository
git clone https://jmhbnz@gitea.jamma.life/jmhbnz/tooling.git ~/Documents/tooling/
# Restore all dotfiles
cp ~/Documents/tooling/.* ~/
# Reload bashrc with updated version
source ~/.bashrcOptional configuration
Optional - Cloud provider tools
Currently kubectl is packaged separately to gcloud and other cloud provider tools so let's install that first.
curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/amd64/kubectl"
sudo install kubectl /usr/local/bin/
which kubectl && kubectl version
rm kubectlFor working with google cloud platform we use the GCP SDK, which provides our cli tools.
# Download the sdk archive
curl -o gcpsdk.tar -O https://dl.google.com/dl/cloudsdk/channels/rapid/downloads/google-cloud-cli-468.0.0-linux-x86_64.tar.gz
# Extract to a folder in path then remove archive
sudo tar xvf gcpsdk.tar -C /usr/local/ && rm gcpsdk.tar
# Correct folder permissions
sudo chown -R $USER:$USER /usr/local/google-cloud-sdk
# Run the install script
/usr/local/google-cloud-sdk/install.shFor working with Amazon Web Services we need the AWS CLI.
# Download the binary
cd ~/Downloads/
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
# Install
unzip awscliv2.zip
sudo ./aws/install
# Clean up
rm -rf ~/Downloads/aws*Optional - Nodejs dev tooling
Some of my project work involves working with nodejs and for package management namely we sometimes use node package manager. The code below installs node 16.x, which is the latest stable release as of <2022-09-16 Fri>.
# Curl down the shell script for adding version 16 of nodejs to apt
sudo curl -sL https://deb.nodesource.com/setup_16.x | sudo bash -
# Install the nodejs package via apt
sudo apt-get install -y nodejs
# Install yarn dependency manager
sudo npm install --global yarnOptional - Install hardware drivers
Optional - Setup humacs editor
An integral part of our pair development workflow is humacs. Below are the instructions to set this up.
# Clone down humacs
git clone --recursive https://github.com/jmhbnz/humacs /home/$USER/Downloads/
# Need to ensure environment variables are set for load path
export EMACSLOADPATH=/home/$USER/Downloads/humacs
Included in this repository is a .bashrc and humacs-custom.el which layer my personal preferences on top of humacs.
Optional - Setup sbp powerline prompt
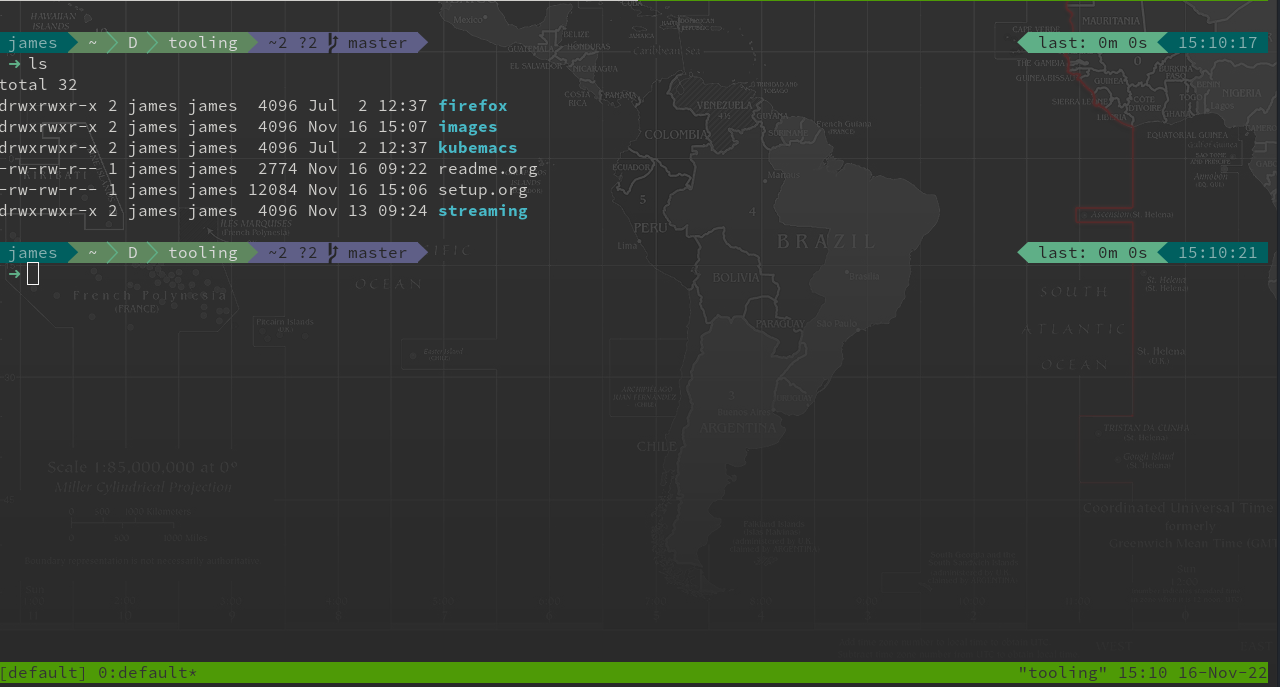
Having an informative bash prompt can ease cognitive burden and make development more pleasant. Below is an example of my terminal prompt which is based on powerline fonts for symbols and simple bash prompt for the overall presentation.
As you can see in the screenshot, contextual "segments" are presented in the prompt to provide information like directory, current user and detailed git status.
To set up this prompt the first thing we need to do is install powerline fonts:
# Install the powerline fonts package
sudo apt-get install fonts-powerline
# Refresh the system font cache
sudo fc-cache --force --verboseOnce powerline fonts are installed we need to install simple bash prompt:
# Clone the repository
git clone https://github.com/jmhbnz/sbp ~/Downloads/sbp/
# Run the install script
/home/$USER/Downloads/sbp/bin/install
# Ensure config directory exists
mkdir --parents /home/$USER/.config/sbp/
# Write the config file
cat << EOF >
#!/usr/bin/env bash
SBP_THEME_COLOR='apathy'
SBP_THEME_LAYOUT='powerline'
# Hooks will run once before every prompt
# Run 'sbp list hooks' to list all available hooks
SBP_HOOKS=('alert')
# Segments are generated before each prompt and can
# be added, removed and reordered
# Run 'sbp list segments' to list all available segments
# Maybe you don't want to run all segments when in
# a small window?
if [[ "$COLUMNS" -le 120 ]]; then
# Let's adjust to the smaller screen
SBP_THEME_LAYOUT='powerline'
SBP_SEGMENTS_LEFT=('path' 'python_env' 'git' 'command')
else
SBP_SEGMENTS_LEFT=('host' 'path' 'python_env' 'k8s' 'git' 'nix')
SBP_SEGMENTS_RIGHT=('command' 'timestamp')
SBP_SEGMENTS_LINE_TWO=('prompt_ready')
fi
# Segment specific settings
SEGMENTS_K8S_DEFAULT_USER="$USER"
SEGMENTS_K8S_HIDE_CLUSTER=1
SEGMENTS_LOAD_THRESHOLD=50
SEGMENTS_LOAD_THRESHOLD_HIGH=80
SEGMENTS_RESCUETIME_REFRESH_RATE=600
SEGMENTS_TIMESTAMP_FORMAT="%H:%M:%S"
SEGMENTS_WTTR_LOCATION='Oslo'
SEGMENTS_WTTR_FORMAT='%p;%t;%w'
EOF
# Reload the prompt
sbp reload
# Disable the k8s segment (it's a bit too long when working with openshift)
sbp toggle peekaboo k8sCongratulations - you should now have a functional, good looking and informative bash prompt! 🎉
Optional - Setup mutt mail client
For reading email we ideally use a cli based client for fast searching and lightweight mail reading.
The mutt mail client fills these roles well for imap mailboxes.
The first step to setup mutt is to ensure it is installed.
sudo apt-get install -y mutt urlscanAfter installing mutt we then need to create configuration directories and files.
mkdir -p ~/.mutt/cache/headers
mkdir ~/.mutt/cache/bodies
touch ~/.mutt/certificatesOne configuration folders and files exist we just need to populate our user mutt configuration file with a configuration for our particular mail provider.
The example provided in this repository utilises the bitwarden cli utility for secrets to ensure these are securely gathered at runtime and not stored in the file.
Optional - Rust dev tooling
I've been tinkering with learning the Rust programming language lately, to set that up follow these steps:
# Ensure pre-requisites are installed
sudo apt install curl build-essential gcc make -y# Install rust via helper script
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | shOnce installed you can check if the rust compiler is installed with the code block below:
rustc -V && cargo -V